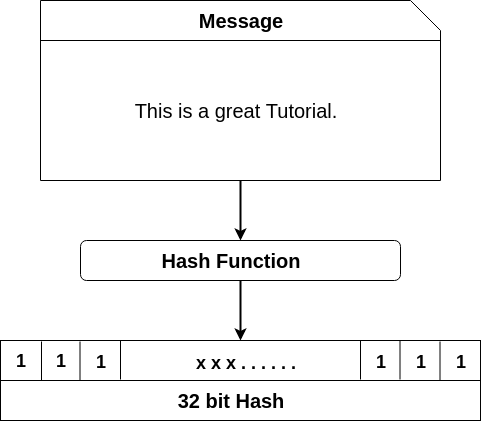
Cryptographic Hash is a Hash function that takes random size input(Text, file…etc) and yields a fixed-size output. It is easy to calculate but challenging to retrieve original data. It is strong and difficult to duplicate the same hash with unique inputs and is a one-way function so revert is not possible.
The SHA (Secure Hash Algorithm) is one of the popular cryptographic hash functions. A cryptographic hash can be used to make a signature for a text or a data file. The SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value.
Properties Of Hash Function
The ideal cryptographic hash function has the following main properties:
- Deterministic: This means that the same message always results in the same hash.
- Quick: It is quick to compute the hash value for any given message.
- Avalanche Effect: This means that every minor change in the message results in a major change in the hash value.
- One-Way Function: You cannot reverse the cryptographic hash function to get to the data.
- Collision Resistance: It is infeasible to find two different messages that produce the same hash value.
Use cases
- Hashing Passwords
You don’t want to store passwords directly into the database
Approach:
- The password should be hashed by hash function which generate unique fixed size output(hash), then we store the hash on the database.
- When the user try to authenticate, we take the password he entered and hash it and verify if the password hash and password hash stored in database are matching, It returns a Boolean value.
- Blockchain
Blockchain is a constantly growing ledger that keeps a permanent record of all the transactions that have taken place, in a secure, chronological and immutable way. To make the data secure blockchain uses hash function. It’s like a fingerprint for each block.
How does the hashing process works?
For this hash function, we are going to use a program developed by Anders Brownworth. This program can be found in the below link.
Anders Brownworth Hash Program: https://anders.com/blockchain/hash.html
Latest posts
Is Data on the Blockchain secure?
